Zero Trust and Your Inbox
There is too much at stake in your business, your life, the life of your team, your customers’ lives to get scammed. It is embarrassing, and it costs you time and money and it could literally be the end of your business. Sadly, the answer is Zero Trust. Zero trust armed with knowledge.
Zero Trust is when you suspect everything, every single email that hits your mailbox, you do not trust it.
But, you say, “That is no way to live.” Maybe not, but here we are in 2023 and scamming is a multi-billion-dollar problem and everyone with an email address, phone number, internet browser, or online account is at risk. This isn’t fear mongering, it is reality, but the antidot to fear is knowledge.
Humans are the weak link in fraud. We make mistakes and willingly give the bad guys critical information that allows them to take advantage of us. It is much easier to rob a bank during business hours, because there is a human behind the counter that has access to what the bad guy wants, verses after hours when everything is locked up.
The intent of this blog is to provide easy to understand knowledge and practical Zero Trust application.
Do not trust any email you get. This isn’t to suggest that we go back to face-to-face communication for everything we do; it is to suggest we learn what a safe email is so we can easily process incoming email as safe or risky. You should be able to know in less than a second if an email warrants further attention as important, phishing, or spam. If you receive one hundred emails in a day, would it be worth 1 min and 40 seconds of your time to be safe?
Phishing and Other Malicious Messages
The most important things to be careful with are attachments and links. If someone sends you an attachment or link to click on, ask yourself, “Do I recognize this email address and am I expecting this attachment or link.” Phishing attacks often come because somebody you know got hacked and the hacker sent an email from that person’s mailbox hoping to catch trusting people unawares. Any attachment or link bears further attention.
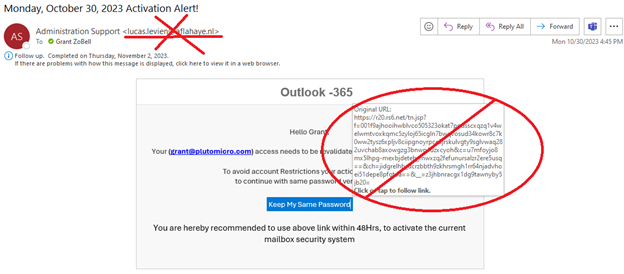
What if it looks legitimate? Then what? Inspect the display name and email address and inspect any links in the email. In the example below, I got an email suggesting I needed to activate my Microsoft 365 account, but the sender is lucas.levien@aflahaye.nl, whom I don’t know, and when I point to the button, it is not taking me to an address that even closely resembles Microsoft 365.
It is very easy to pretend to be somebody you are not over email. It is like someone putting a name tag on their shirt with your name on it, but anybody who knows you will spot the fraud. In an email, on the “From” line, you will usually see the name of the person it is from and the email address of that person in angle brackets, like this: Grant ZoBell <grant@plutomicro.com>
In the example above, someone is trying to phish me from the payroll department. The display name suggests the payroll department, but the following email address (comms@tadel.com) isn’t anything to do with the Pluto Payroll department. The attachment carries a link with a malicious payload. That, my friends, is phishing. Delete it.
Perhaps you’ve inspected the From address, and it looks good, now it is time to inspect any link in the email itself. To inspect a web link in an email, hover over it with your mouse cursor, and the actual address the link takes you to will pop out, or if you are using webmail, it will appear in the bottom bar of your browser. This is more difficult on a phone; to inspect the link on a phone, tap and hold the link and preview will popup; however, if there is any doubt, just wait until you are at your computer to inspect the link.
What you are looking for, when you inspect a link, is that the link matches what is written in the email. Say you receive an email asking you to check out an Amazon store item, but when you hover over the link the website is http://nothing-resembling-amazon-dot.ca; that is phishing.
SPAM
So far, we’ve only talked about phishing, but just as annoying, albeit less malicious, is SPAM. SPAM is part of your human powered insta-filter: is it important, phishing, or SPAM?
SPAM can be categorized into two categories: solicited or unsolicited. In the past, unwanted mail was on paper in a mailbox, or maybe on a fax machine. Now we get junk email from people who we knowingly gave our email addresses to and junk mail from people who got our address a different way. Either way, do not stress about how or why you got junk mail, just identify it and deal with it in milliseconds like you used to at the Post Office.
With a lot of the SPAM messages you receive, you can easily identify who sent the email, and that you probably shared your email address with them. Delete the message if the subject is irrelevant. If you are getting too much email from this known sender, look for the unsubscribe link at the bottom of the email and use it. If the message might be useful, flag it for later review.
Some SPAM is less obvious and even could be confused with phishing, so apply the principles of phishy emails: be careful of attachments and inspect links. When inspecting links, the links most likely will be different than whatever company you’re getting email from because they will be coming from their mass email application. Examples of mass email apps are Mail Chimp and Hub Spot; these are legitimate emails, perhaps unwanted, but not necessarily phishing. When in doubt just delete the message like you throw away unsolicited paper mail.
Important Messages
Now that you’ve filtered your email in record time, the next fail point is you. Having deleted the phishing and irrelevant SPAM, what is left in your inbox are benign messages and important messages. Obviously, you can’t process every important message in your Inbox, and email comes in hourly. You cannot trust yourself to remember every email that needs further attention.
When you’ve determined that an email needs a response or further review, either respond immediately or mark that message for future attention. In Outlook you can check the flag icon on a particular message and in Outlook online you can pin it. In Gmail and Google Workspace, you can star the message or mark it as important. When you’ve responded or reviewed a message, remove its flag. Periodically in the day or week, check your marked messages to see what you may or may not need to do.
Other Media
Zero Trust applies to other ways people want to grab your attention or steal your information and money.
Don’t trust any phone calls you get where the party on the other side is asking you for sensitive information, especially if that information could be used to gain access to financial resources. Hang up and make your own phone call to verify.
Don’t trust unsolicited text messages, or conversations, especially if has a link; delete it. There is nothing in a text link that is going to change your life for the better.
Don’t trust pop-ups on websites unless you 100% certain about the website. Lately, I’ve seen benign Google searches result in websites that are simply malicious. I’ve seen other perfectly normal websites with malicious ads. If it looks like clickbait, stay away from it.
Artificial Intelligence: The Good, the Bad, and the Ugly
This isn’t about ChatGPT or CoPilot, we’ll talk about that in our next blog. This is still about your Inbox and Zero Trust.
We don’t know how much crud doesn’t even get close to our Inbox, artificial intelligence takes care of a lot of malicious content. That being said, you get what you pay for. Microsoft and 3rd party providers have more advanced paid filtering services that can prevent more unsolicited email and detect phishing with more accuracy. Pluto Micro can help with this, ask your I.T. service provider if you aren’t a Pluto Micro customer yet.
No matter how good A.I. is and how much you paid, it still isn’t going to filter every phish and every SPAM. That is where you’re human power filter comes in. Is it phishing, is it SPAM, is it important.
No matter how good your A.I. is, it still makes mistakes and filters messages that shouldn’t be filtered. In the tech world we call these mistakes false positives, but you know them as your Junk Email folder (Microsoft Outlook) or SPAM folder (Gmail). Some email filters quarantine messages before they even hit your mail folders. It is a good idea to periodically review your Junk or SPAM folders and know how to access your quarantine.
To see your Junk Mail folder on Microsoft 365, click https://outlook.office.com/mail/junkemail .
To see your quarantine on Microsoft 365, click https://security.microsoft.com/quarantine .
To see your SPAM folder on Gmail, click https://mail.google.com/mail/u/0/#spam .
As AI gets more and more advanced, the bad guys are using it in ways we only thought were in the movies. Recently AI was used to deep fake a video meeting with multiple decision makers instructing a multi-million dollar financial transaction from the business’s bank account. If it seems phishy and your spidey sense is telling you something seems off, stop the flow of the interaction. Verify it in a different way. If somebody is on the phone, hang up and send an email; if somebody is emailing you instructions that seem off, call them. If you’re unsure, ask your I.T. service provider for their opinion.
Conclusion
There is too much at risk in our lives and business not to be vigilant about our inbox, however, we should not live in fear. There is nothing in our inbox that can hurt us without us allowing it; our responsibility is to learn how to recognize if a message is malicious (phishing), benign (SPAM), or important and needs further review.